| Table of Contents |
|---|
Key Points
References
...
ipfs-medium.com-IPFS with React Loading IPFS Assets from Your Distributed IPFS Gateways.pdf
...
ipfs-medium.com-Introduction to IPFS Run Nodes on Your Network with HTTP Gateways.pdf
...
https://www.yahoo.com/lifestyle/best-vpn-services-150213463.html
vpn-2022-The best VPN services to protect your privacy in 2022.pdf file
...
Key Concepts
OSI Communication Layers Model
https://searchnetworking.techtarget.com/definition/OSI
OSI (Open Systems Interconnection) is a reference model for how applications communicate over a network.
A reference model is a conceptual framework for understanding relationships. The purpose of the OSI reference model is to guide vendors and developers so the digital communication products and software programs they create can interoperate, and to facilitate a clear framework that describes the functions of a networking or telecommunication system.
Most vendors involved in telecommunications make an attempt to describe their products and services in relation to the OSI model. And although it is useful for guiding discussion and evaluation, OSI is rarely actually implemented as-is. That's because few network products or standard tools keep related functions together in well-defined layers, as is the case in the OSI model. The TCP/IP protocol suite, which defines the internet, does not map cleanly to the OSI model.
How the OSI model works
IT professionals use OSI to model or trace how data is sent or received over a network. This model breaks down data transmission over a series of seven layers, each of which is responsible for performing specific tasks concerning sending and receiving data.
The main concept of OSI is that the process of communication between two endpoints in a network can be divided into seven distinct groups of related functions, or layers. Each communicating user or program is on a device that can provide those seven layers of function.
In this architecture, each layer serves the layer above it and, in turn, is served by the layer below it. So, in a given message between users, there will be a flow of data down through the layers in the source computer, across the network, and then up through the layers in the receiving computer. Only the application layer, at the top of the stack, doesn’t provide services to a higher-level layer.
The seven layers of function are provided by a combination of applications, operating systems, network card device drivers and networking hardware that enable a system to transmit a signal over a network Ethernet or fiber optic cable or through Wi-Fi or other wireless protocols.
TechTarget
7 layers of the OSI model
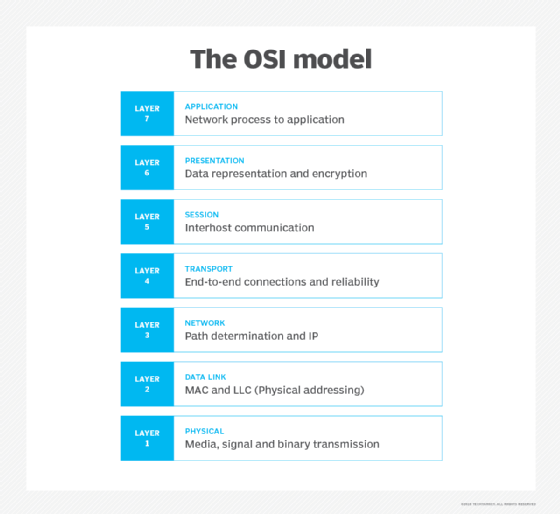
The seven Open Systems Interconnection layers are:
Layer 7: The application layer: Enables the user (human or software) to interact with the application or network whenever the user elects to read messages, transfer files or perform other network-related activities. Web browsers and other internet-connected apps, such as Outlook and Skype, use Layer 7 application protocols.
Layer 6: The presentation layer: Translates or formats data for the application layer based on the semantics or syntax that the application accepts. This layer is also able to handle the encryption and decryption that the application layer requires.
Layer 5: The session layer: Sets up, coordinates and terminates conversations between applications. Its services include authentication and reconnection after an interruption. This layer determines how long a system will wait for another application to respond. Examples of session layer protocols include X.225, AppleTalk and Zone Information Protocol (ZIP).
Layer 4: The transport layer: Is responsible for transferring data across a network and provides error-checking mechanisms and data flow controls. It determines how much data to send, where it gets sent and at what rate. The Transmission Control Protocol is the best known example of the transport layer.
Layer 3: The network layer: Primary function is to move data into and through other networks. Network layer protocols accomplish this by packaging data with correct network address information, selecting the appropriate network routes and forwarding the packaged data up the stack to the transport layer.
Layer 2: The data-link layer: The protocol layer in a program that handles the moving of data into and out of a physical link in a network. This layer handles problems that occur as a result of bit transmission errors. It ensures that the pace of the data flow doesn’t overwhelm the sending and receiving devices. This layer also permits the transmission of data to Layer 3, the network layer, where it is addressed and routed.
Layer 1: The physical layer: Transports data using electrical, mechanical or procedural interfaces. This layer is responsible for sending computer bits from one device to another along the network. It determines how physical connections to the network are set up and how bits are represented into predictable signals as they are transmitted either electrically, optically or via radio waves.
Cross layer functions
Cross-layer functions, services that may affect more than one layer, include:
- Security service (telecommunication) as defined by ITU-T X.800 recommendation.
- Management functions -- functions that enable the configuration, instantiation, monitoring and terminating of the communications of two or more entities.
- Multiprotocol Label Switching (MPLS) -- operates at an OSI-model layer that lies between layer 2 (data link layer) and layer 3 (network layer). MPLS can be used to carry a variety of traffic, including Ethernet frames and IP packets.
- ARP -- translates IPv4 addresses (OSI layer 3) into Ethernet MAC addresses (OSI layer 2).
- Domain name service – an application layer service used to look up the IP address of a domain name.
History of the OSI model
Developed by representatives of major computer and telecommunication companies beginning in 1983, OSI was originally intended to be a detailed specification of actual interfaces. Instead, the committee decided to establish a common reference model that others could then use to develop detailed interfaces, which, in turn, could become standards governing the transmission of data packets. The OSI architecture was officially adopted as an international standard by the International Organization for Standardization (ISO) in 1984.
OSI model vs. TCP/IP model
OSI is a reference model that describes the functions of a telecommunication or networking system, while TCP/IP is a suite of communication protocols used to interconnect network devices on the internet. TCP/IP and OSI are the most broadly used networking models for communication.
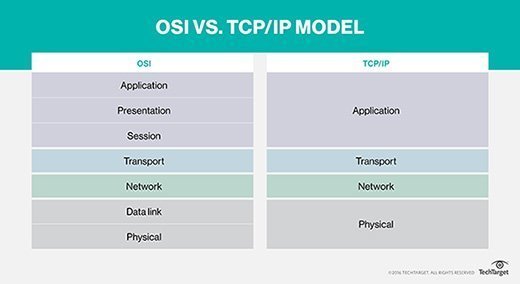
The OSI and TCP/IP models have similarities and differences. The main similarity is in their construction as both use layers, although the OSI model consists of seven layers, while TCP/IP consists of just four layers.
Another similarity is that the upper layer for each model is the application layer, which performs the same tasks in each model, but may vary according to the information each receives.
The functions performed in each model are also similar because each uses a network layer and transport to operate. The OSI and TCP/IP model are each mostly used to transmit data packets. Although they will do so by different means and by different paths, they will still reach their destinations.
The OSI and TCP/IP models are similar in that they:
- are logical models.
- define standards for networking.
- divide the network communication process in layers.
- provide frameworks for creating and implementing networking standards and devices.
- enable one manufacturer to make devices and network components that can coexist and work with the devices and components made by other manufacturers.
- divide complex functions into simpler components.
Differences between the OSI model and TCP/IP model include:
- OSI has seven layers while the TCP/IP has four layers.
- OSI uses three layers (application, presentation and session) to define the functionality of upper layers, while TCP/IP uses just one layer (application).
- OSI uses two separate layers (physical and data link) to define the functionality of the bottom layers while TCP/IP uses one layer (link).
- OSI uses the network layer to define the routing standards and protocols, while TCP/IP uses the Internet layer.
Pros and cons of the OSI model
The OSI model has a number of advantages, including:
- It’s considered a standard model in computer networking.
- Supports connectionless as well as connection-oriented services. Users can leverage connectionless services when they need faster data transmissions over the internet and the connection-oriented model when they’re looking for reliability.
- Has the flexibility to adapt to many protocols
- More adaptable and secure than having all services bundled in one layer.
The disadvantages include:
- Doesn’t define any particular protocol.
- Session layer, which is used for session management, and the presentation layer, which deals with user interaction aren’t as useful as other layers in the OSI model.
- Some services are duplicated at various layers, such as the transport and data link layers each have an error control mechanism.
- Layers can’t work in parallel; each layer has to wait to receive data from the previous layer.
https://en.wikipedia.org/wiki/OSI_model
Network Layers
https://www.geeksforgeeks.org/difference-between-layer-2-and-layer-3-switches/
Layer 2 = local area network - LAN
MAC, TokenRing or TokenBus
Layer 3 = wide area network - WAN
TCP, UDP, SNA, BSC, ASC etc
TCP/IP
TCP tutorial IBM - 2006 - comprehensive resource
TCP Network Model
https://searchnetworking.techtarget.com/definition/TCP-IP
TCP/IP, or the Transmission Control Protocol/Internet Protocol, is a suite of communication protocols used to interconnect network devices on the internet. TCP/IP can also be used as a communications protocol in a private computer network (an intranet or an extranet).
The entire Internet Protocol suite -- a set of rules and procedures -- is commonly referred to as TCP/IP, though others are included in the suite. The TCP/IP protocol suite functions as an abstraction layer between internet applications and the routing/switching fabric.
TCP/IP specifies how data is exchanged over the internet by providing end-to-end communications that identify how it should be broken into packets, addressed, transmitted, routed and received at the destination. TCP/IP requires little central management, and it is designed to make networks reliable, with the ability to recover automatically from the failure of any device on the network.
The two main protocols in the Internet Protocol suite serve specific functions. TCP defines how applications can create channels of communication across a network. It also manages how a message is assembled into smaller packets before they are then transmitted over the internet and reassembled in the right order at the destination address.
IP defines how to address and route each packet to make sure it reaches the right destination. Each gateway computer on the network checks this IP address to determine where to forward the message.
A subnet mask is what tells a computer, or other network device, what portion of the IP address is used to represent the network and what part is used to represent hosts (other computers) on the network.
A Network Address Translator (NAT) is the virtualization of Internet Protocol addresses. NAT helps improve security and decrease the number of IP addresses an organization needs.
Common types of TCP/IP include the following:
- HTTP (Hyper Text Transfer Protocol) handles the communication between a web server and a web browser.
- HTTPS (Secure HTTP) handles secure communication between a web server and a web browser.
- FTP (File Transfer Protocol) handles transmission of files between computers.
How TCP/IP works
TCP/IP uses the client-server model of communication in which a user or machine (a client) is provided a service (like sending a webpage) by another computer (a server) in the network.
Collectively, the TCP/IP suite of protocols is classified as stateless, which means each client request is considered new because it is unrelated to previous requests. Being stateless frees up network paths so they can be used continuously.
The transport layer itself, however, is stateful. It transmits a single message, and its connection remains in place until all the packets in a message have been received and reassembled at the destination.
The TCP/IP model differs slightly from the seven-layer Open Systems Interconnection (OSI) networking model designed after it. The OSI reference model defines how applications can communicate over a network.
TCP/IP model layers
TCP/IP functionality is divided into four layers, each of which include specific protocols:
- The application layer provides applications with standardized data exchange. Its protocols include the HTTP, FTP, Post Office Protocol 3 (POP3), Simple Mail Transfer Protocol (SMTP) and Simple Network Management Protocol (SNMP). At the application layer, the payload is the actual application data.
- The transport layer is responsible for maintaining end-to-end communications across the network. TCP handles communications between hosts and provides flow control, multiplexing and reliability. The transport protocols include TCP and User Datagram Protocol (UDP), which is sometimes used instead of TCP for special purposes.
- The network layer, also called the internet layer, deals with packets and connects independent networks to transport the packets across network boundaries. The network layer protocols are the IP and the Internet Control Message Protocol (ICMP), which is used for error reporting.
- The physical layer, also known as the network interface layer or data link layer, consists of protocols that operate only on a link -- the network component that interconnects nodes or hosts in the network. The protocols in this lowest layer include Ethernet for local area networks (LANs) and the Address Resolution Protocol (ARP).
Importance of TCP/IP
TCP/IP is nonproprietary and, as a result, is not controlled by any single company. Therefore, the Internet Protocol suite can be modified easily. It is compatible with all operating systems, so it can communicate with any other system. The Internet Protocol suite is also compatible with all types of computer hardware and networks
TCP/IP is highly scalable and, as a routable protocol, can determine the most efficient path through the network. It is widely used in current internet architecture.
The history of TCP/IP
The Defense Advanced Research Projects Agency (DARPA), the research branch of the U.S. Department of Defense, created the TCP/IP model in the 1970s for use in ARPANET, a wide area network that preceded the internet. TCP/IP was originally designed for the Unix operating system, and it has been built into all of the operating systems that came after it.
The TCP/IP model and its related protocols are now maintained by the Internet Engineering Task Force.
TCP/IP vs. OSI model
TCP/IP and OSI are the most widely used communication networking protocols. The main difference is that OSI is a conceptual model that's not practically used for communication. Rather, it defines how applications can communicate over a network. TCP/IP, on the other hand, is widely used to establish links and network interaction.
The TCP/IP protocols lay out standards on which the internet was created, while the OSI model provides guidelines on how communication has to be done. Therefore, TCP/IP is a more practical model.
The TCP/IP and OSI models have similarities and differences. The main similarity is in the way they are constructed as both use layers, although the TCP/IP consists of just four layers, while the OSI model consists of seven layers.
These are the seven layers of the OSI model:
- Layer 7, the application layer, lets the user (software or human) interact with the application or network when the user wants to read messages, transfer files or engage in other network-related activities.
- Layer 6, the presentation layer, translates or formats data for the application layer based on the semantics or syntax that the app accepts.
- Layer 5, the session layer, sets up, coordinates and terminates conversations between apps.
- Layer 4, the transport layer, handles transferring data across a network and providing error-checking mechanisms and data flow controls.
- Layer 3, the network layer, moves data into and through other networks.
- Layer 2, the data-link layer, handles problems that occur as a result of bit transmission errors.
- Layer 1, the physical layer, transports data using electrical, mechanical or procedural interfaces.
The upper layer for both the TCP/IP model and the OSI model is the application layer. Although this layer performs the same tasks in each model, those tasks may vary depending on the data each receives.
The functions performed in each model are also similar because each uses a network layer and transport to operate. The TCP/IP and OSI models are each mostly used to transmit data packets. Although they will do so by different means and by different paths, they will still reach their destinations.
The similarities between the TCP/IP model and the OSI model include the following:
- They are both logical models.
- They define networking standards.
- They divide the network communication process in layers.
- They provide frameworks for creating and implementing networking standards and devices.
- They enable one manufacturer to make devices and network components that can coexist and work with the devices and components made by other manufacturers.
The differences between the TCP/IP model and the OSI model include the following:
- TCP/IP uses just one layer (application) to define the functionalities of the upper layers, while the OSI model uses three layers (application, presentation and session).
- The TCP/IP model uses one layer (link) to define the functionalities of the bottom layers, while the OSI uses two layers (physical and data link).
- The TCP/IP model use the internet layer to define the routing standards and protocols, while OSI uses the network layer.
- The TCP/IP header size is 20 bytes while the OSI header is 5 bytes.
- The TCP/IP model is a protocol-oriented standard, whereas the OSI model is a generic model based on the functionalities of each layer.
- TCP/IP follows a horizontal approach, while OSI follows a vertical approach.
- In the TCP/IP suite, the protocols were developed first, and then the model was developed. In OSI, the model was developed first, and then the protocols in each layer were developed.
- TCP/IP helps establish a connection between different types of computers, whereas the OSI model helps standardize routers, switches, motherboards and other hardware.
Uses of TCP/IP
TCP/IP can be used to provide remote login over the network, for interactive file transfer, to deliver email, to deliver webpages over the network and to remotely access a server host's file system.
Pros and cons of TCP/IP
The advantages of using the TCP/IP model include the following:
- helps establish a connection between different types of computers;
- works independently of the operating system;
- supports many routing protocols;
- has client-server architecture that is highly scalable;
- can be operated independently;
- supports several routing protocols; and
- is lightweight and doesn't place unnecessary strain on a network or computer.
The disadvantages of TCP/IP include the following:
- complicated to set up and manage;
- transport layer doesn't guarantee delivery of packets;
- not easy to replace protocols in TCP/IP;
- doesn't clearly separate the concepts of services, interfaces and protocols so not good for describing new technologies in new networks; and
- especially vulnerable to a SYN (synchronization) attack, which is a type of denial-of-service attack in which a bad actor uses TCP/IP protocol.
HTTPS
HTML definitions include the options to run HTTP2 services
https://html.spec.whatwg.org/multipage/server-sent-events.html
migrating to HTTP2
https://dev.to/lek890/the-http-1-1-to-http-2-transition-for-web-apps-2bjm
routing HTTP2 traffic ( Tanzu concepts only )
https://docs.pivotal.io/application-service/2-12/devguide/http2-protocol.html
HTTP2 features and design
https://www.smashingmagazine.com/2016/02/getting-ready-for-http2/
HTTP2 features:
- allow concurrent requests across a single TCP connection, known as multiplexing;
- allow browsers to prioritize assets so that resources vital to the display of a page could be sent by the server first;
- compress and reduce HTTP headers;
- implement server push, whereby a server can push vital resources to the browser before being asked for them.
Confirm that a server app and Chrome are running HTTP2 not falling back to HTTP1
Is the client app and server running HTTP2? ( required for useful SSE without connection limits over the single TLS connection )
for chrome browser, validate the app is running on a TLS server using HTTP2
chrome://net-internals/#http2 creates an option to capture http logs to file - scan for HTTP2 in log
| Table of Contents |
|---|
Key Points
References
| Reference_description_with_linked_URLs____________________________ | Notes_____________________________________________________________ |
|---|---|
| TCP tutorial IBM - 2006 - comprehensive resource | |
| Articles | |
ipfs-medium.com-IPFS with React Loading IPFS Assets from Your Distributed IPFS Gateways.pdf | IPFS with React: Loading IPFS Assets from Your Distributed IPFS Gateways |
ipfs-medium.com-Introduction to IPFS Run Nodes on Your Network with HTTP Gateways.pdf | Introduction to IPFS: Run Nodes on Your Network, with HTTP Gateways |
https://www.yahoo.com/lifestyle/best-vpn-services-150213463.html vpn-2022-The best VPN services to protect your privacy in 2022.pdf file | VPN options for private connections ** |
Key Concepts
OSI Communication Layers Model
https://searchnetworking.techtarget.com/definition/OSI
OSI (Open Systems Interconnection) is a reference model for how applications communicate over a network.
A reference model is a conceptual framework for understanding relationships. The purpose of the OSI reference model is to guide vendors and developers so the digital communication products and software programs they create can interoperate, and to facilitate a clear framework that describes the functions of a networking or telecommunication system.
Most vendors involved in telecommunications make an attempt to describe their products and services in relation to the OSI model. And although it is useful for guiding discussion and evaluation, OSI is rarely actually implemented as-is. That's because few network products or standard tools keep related functions together in well-defined layers, as is the case in the OSI model. The TCP/IP protocol suite, which defines the internet, does not map cleanly to the OSI model.
How the OSI model works
IT professionals use OSI to model or trace how data is sent or received over a network. This model breaks down data transmission over a series of seven layers, each of which is responsible for performing specific tasks concerning sending and receiving data.
The main concept of OSI is that the process of communication between two endpoints in a network can be divided into seven distinct groups of related functions, or layers. Each communicating user or program is on a device that can provide those seven layers of function.
In this architecture, each layer serves the layer above it and, in turn, is served by the layer below it. So, in a given message between users, there will be a flow of data down through the layers in the source computer, across the network, and then up through the layers in the receiving computer. Only the application layer, at the top of the stack, doesn’t provide services to a higher-level layer.
The seven layers of function are provided by a combination of applications, operating systems, network card device drivers and networking hardware that enable a system to transmit a signal over a network Ethernet or fiber optic cable or through Wi-Fi or other wireless protocols.
TechTarget
7 layers of the OSI model
The seven Open Systems Interconnection layers are:
Layer 7: The application layer: Enables the user (human or software) to interact with the application or network whenever the user elects to read messages, transfer files or perform other network-related activities. Web browsers and other internet-connected apps, such as Outlook and Skype, use Layer 7 application protocols.
Layer 6: The presentation layer: Translates or formats data for the application layer based on the semantics or syntax that the application accepts. This layer is also able to handle the encryption and decryption that the application layer requires.
Layer 5: The session layer: Sets up, coordinates and terminates conversations between applications. Its services include authentication and reconnection after an interruption. This layer determines how long a system will wait for another application to respond. Examples of session layer protocols include X.225, AppleTalk and Zone Information Protocol (ZIP).
Layer 4: The transport layer: Is responsible for transferring data across a network and provides error-checking mechanisms and data flow controls. It determines how much data to send, where it gets sent and at what rate. The Transmission Control Protocol is the best known example of the transport layer.
Layer 3: The network layer: Primary function is to move data into and through other networks. Network layer protocols accomplish this by packaging data with correct network address information, selecting the appropriate network routes and forwarding the packaged data up the stack to the transport layer.
Layer 2: The data-link layer: The protocol layer in a program that handles the moving of data into and out of a physical link in a network. This layer handles problems that occur as a result of bit transmission errors. It ensures that the pace of the data flow doesn’t overwhelm the sending and receiving devices. This layer also permits the transmission of data to Layer 3, the network layer, where it is addressed and routed.
Layer 1: The physical layer: Transports data using electrical, mechanical or procedural interfaces. This layer is responsible for sending computer bits from one device to another along the network. It determines how physical connections to the network are set up and how bits are represented into predictable signals as they are transmitted either electrically, optically or via radio waves.
Cross layer functions
Cross-layer functions, services that may affect more than one layer, include:
- Security service (telecommunication) as defined by ITU-T X.800 recommendation.
- Management functions -- functions that enable the configuration, instantiation, monitoring and terminating of the communications of two or more entities.
- Multiprotocol Label Switching (MPLS) -- operates at an OSI-model layer that lies between layer 2 (data link layer) and layer 3 (network layer). MPLS can be used to carry a variety of traffic, including Ethernet frames and IP packets.
- ARP -- translates IPv4 addresses (OSI layer 3) into Ethernet MAC addresses (OSI layer 2).
- Domain name service – an application layer service used to look up the IP address of a domain name.
History of the OSI model
Developed by representatives of major computer and telecommunication companies beginning in 1983, OSI was originally intended to be a detailed specification of actual interfaces. Instead, the committee decided to establish a common reference model that others could then use to develop detailed interfaces, which, in turn, could become standards governing the transmission of data packets. The OSI architecture was officially adopted as an international standard by the International Organization for Standardization (ISO) in 1984.
OSI model vs. TCP/IP model
OSI is a reference model that describes the functions of a telecommunication or networking system, while TCP/IP is a suite of communication protocols used to interconnect network devices on the internet. TCP/IP and OSI are the most broadly used networking models for communication.
The OSI and TCP/IP models have similarities and differences. The main similarity is in their construction as both use layers, although the OSI model consists of seven layers, while TCP/IP consists of just four layers.
Another similarity is that the upper layer for each model is the application layer, which performs the same tasks in each model, but may vary according to the information each receives.
The functions performed in each model are also similar because each uses a network layer and transport to operate. The OSI and TCP/IP model are each mostly used to transmit data packets. Although they will do so by different means and by different paths, they will still reach their destinations.
The OSI and TCP/IP models are similar in that they:
- are logical models.
- define standards for networking.
- divide the network communication process in layers.
- provide frameworks for creating and implementing networking standards and devices.
- enable one manufacturer to make devices and network components that can coexist and work with the devices and components made by other manufacturers.
- divide complex functions into simpler components.
Differences between the OSI model and TCP/IP model include:
- OSI has seven layers while the TCP/IP has four layers.
- OSI uses three layers (application, presentation and session) to define the functionality of upper layers, while TCP/IP uses just one layer (application).
- OSI uses two separate layers (physical and data link) to define the functionality of the bottom layers while TCP/IP uses one layer (link).
- OSI uses the network layer to define the routing standards and protocols, while TCP/IP uses the Internet layer.
Pros and cons of the OSI model
The OSI model has a number of advantages, including:
- It’s considered a standard model in computer networking.
- Supports connectionless as well as connection-oriented services. Users can leverage connectionless services when they need faster data transmissions over the internet and the connection-oriented model when they’re looking for reliability.
- Has the flexibility to adapt to many protocols
- More adaptable and secure than having all services bundled in one layer.
The disadvantages include:
- Doesn’t define any particular protocol.
- Session layer, which is used for session management, and the presentation layer, which deals with user interaction aren’t as useful as other layers in the OSI model.
- Some services are duplicated at various layers, such as the transport and data link layers each have an error control mechanism.
- Layers can’t work in parallel; each layer has to wait to receive data from the previous layer.
https://en.wikipedia.org/wiki/OSI_model
Network Layers
https://www.geeksforgeeks.org/difference-between-layer-2-and-layer-3-switches/
Layer 2 = local area network - LAN
MAC, TokenRing or TokenBus
Layer 3 = wide area network - WAN
TCP, UDP, SNA, BSC, ASC etc
TCP/IP
TCP tutorial IBM - 2006 - comprehensive resource
TCP Network Model
https://searchnetworking.techtarget.com/definition/TCP-IP
TCP/IP, or the Transmission Control Protocol/Internet Protocol, is a suite of communication protocols used to interconnect network devices on the internet. TCP/IP can also be used as a communications protocol in a private computer network (an intranet or an extranet).
The entire Internet Protocol suite -- a set of rules and procedures -- is commonly referred to as TCP/IP, though others are included in the suite. The TCP/IP protocol suite functions as an abstraction layer between internet applications and the routing/switching fabric.
TCP/IP specifies how data is exchanged over the internet by providing end-to-end communications that identify how it should be broken into packets, addressed, transmitted, routed and received at the destination. TCP/IP requires little central management, and it is designed to make networks reliable, with the ability to recover automatically from the failure of any device on the network.
The two main protocols in the Internet Protocol suite serve specific functions. TCP defines how applications can create channels of communication across a network. It also manages how a message is assembled into smaller packets before they are then transmitted over the internet and reassembled in the right order at the destination address.
IP defines how to address and route each packet to make sure it reaches the right destination. Each gateway computer on the network checks this IP address to determine where to forward the message.
A subnet mask is what tells a computer, or other network device, what portion of the IP address is used to represent the network and what part is used to represent hosts (other computers) on the network.
A Network Address Translator (NAT) is the virtualization of Internet Protocol addresses. NAT helps improve security and decrease the number of IP addresses an organization needs.
Common types of TCP/IP include the following:
- HTTP (Hyper Text Transfer Protocol) handles the communication between a web server and a web browser.
- HTTPS (Secure HTTP) handles secure communication between a web server and a web browser.
- FTP (File Transfer Protocol) handles transmission of files between computers.
How TCP/IP works
TCP/IP uses the client-server model of communication in which a user or machine (a client) is provided a service (like sending a webpage) by another computer (a server) in the network.
Collectively, the TCP/IP suite of protocols is classified as stateless, which means each client request is considered new because it is unrelated to previous requests. Being stateless frees up network paths so they can be used continuously.
The transport layer itself, however, is stateful. It transmits a single message, and its connection remains in place until all the packets in a message have been received and reassembled at the destination.
The TCP/IP model differs slightly from the seven-layer Open Systems Interconnection (OSI) networking model designed after it. The OSI reference model defines how applications can communicate over a network.
TCP/IP model layers
TCP/IP functionality is divided into four layers, each of which include specific protocols:
- The application layer provides applications with standardized data exchange. Its protocols include the HTTP, FTP, Post Office Protocol 3 (POP3), Simple Mail Transfer Protocol (SMTP) and Simple Network Management Protocol (SNMP). At the application layer, the payload is the actual application data.
- The transport layer is responsible for maintaining end-to-end communications across the network. TCP handles communications between hosts and provides flow control, multiplexing and reliability. The transport protocols include TCP and User Datagram Protocol (UDP), which is sometimes used instead of TCP for special purposes.
- The network layer, also called the internet layer, deals with packets and connects independent networks to transport the packets across network boundaries. The network layer protocols are the IP and the Internet Control Message Protocol (ICMP), which is used for error reporting.
- The physical layer, also known as the network interface layer or data link layer, consists of protocols that operate only on a link -- the network component that interconnects nodes or hosts in the network. The protocols in this lowest layer include Ethernet for local area networks (LANs) and the Address Resolution Protocol (ARP).
Importance of TCP/IP
TCP/IP is nonproprietary and, as a result, is not controlled by any single company. Therefore, the Internet Protocol suite can be modified easily. It is compatible with all operating systems, so it can communicate with any other system. The Internet Protocol suite is also compatible with all types of computer hardware and networks
TCP/IP is highly scalable and, as a routable protocol, can determine the most efficient path through the network. It is widely used in current internet architecture.
The history of TCP/IP
The Defense Advanced Research Projects Agency (DARPA), the research branch of the U.S. Department of Defense, created the TCP/IP model in the 1970s for use in ARPANET, a wide area network that preceded the internet. TCP/IP was originally designed for the Unix operating system, and it has been built into all of the operating systems that came after it.
The TCP/IP model and its related protocols are now maintained by the Internet Engineering Task Force.
TCP/IP vs. OSI model
TCP/IP and OSI are the most widely used communication networking protocols. The main difference is that OSI is a conceptual model that's not practically used for communication. Rather, it defines how applications can communicate over a network. TCP/IP, on the other hand, is widely used to establish links and network interaction.
The TCP/IP protocols lay out standards on which the internet was created, while the OSI model provides guidelines on how communication has to be done. Therefore, TCP/IP is a more practical model.
The TCP/IP and OSI models have similarities and differences. The main similarity is in the way they are constructed as both use layers, although the TCP/IP consists of just four layers, while the OSI model consists of seven layers.
These are the seven layers of the OSI model:
- Layer 7, the application layer, lets the user (software or human) interact with the application or network when the user wants to read messages, transfer files or engage in other network-related activities.
- Layer 6, the presentation layer, translates or formats data for the application layer based on the semantics or syntax that the app accepts.
- Layer 5, the session layer, sets up, coordinates and terminates conversations between apps.
- Layer 4, the transport layer, handles transferring data across a network and providing error-checking mechanisms and data flow controls.
- Layer 3, the network layer, moves data into and through other networks.
- Layer 2, the data-link layer, handles problems that occur as a result of bit transmission errors.
- Layer 1, the physical layer, transports data using electrical, mechanical or procedural interfaces.
The upper layer for both the TCP/IP model and the OSI model is the application layer. Although this layer performs the same tasks in each model, those tasks may vary depending on the data each receives.
The functions performed in each model are also similar because each uses a network layer and transport to operate. The TCP/IP and OSI models are each mostly used to transmit data packets. Although they will do so by different means and by different paths, they will still reach their destinations.
The similarities between the TCP/IP model and the OSI model include the following:
- They are both logical models.
- They define networking standards.
- They divide the network communication process in layers.
- They provide frameworks for creating and implementing networking standards and devices.
- They enable one manufacturer to make devices and network components that can coexist and work with the devices and components made by other manufacturers.
The differences between the TCP/IP model and the OSI model include the following:
- TCP/IP uses just one layer (application) to define the functionalities of the upper layers, while the OSI model uses three layers (application, presentation and session).
- The TCP/IP model uses one layer (link) to define the functionalities of the bottom layers, while the OSI uses two layers (physical and data link).
- The TCP/IP model use the internet layer to define the routing standards and protocols, while OSI uses the network layer.
- The TCP/IP header size is 20 bytes while the OSI header is 5 bytes.
- The TCP/IP model is a protocol-oriented standard, whereas the OSI model is a generic model based on the functionalities of each layer.
- TCP/IP follows a horizontal approach, while OSI follows a vertical approach.
- In the TCP/IP suite, the protocols were developed first, and then the model was developed. In OSI, the model was developed first, and then the protocols in each layer were developed.
- TCP/IP helps establish a connection between different types of computers, whereas the OSI model helps standardize routers, switches, motherboards and other hardware.
Uses of TCP/IP
TCP/IP can be used to provide remote login over the network, for interactive file transfer, to deliver email, to deliver webpages over the network and to remotely access a server host's file system.
Pros and cons of TCP/IP
The advantages of using the TCP/IP model include the following:
- helps establish a connection between different types of computers;
- works independently of the operating system;
- supports many routing protocols;
- has client-server architecture that is highly scalable;
- can be operated independently;
- supports several routing protocols; and
- is lightweight and doesn't place unnecessary strain on a network or computer.
The disadvantages of TCP/IP include the following:
- complicated to set up and manage;
- transport layer doesn't guarantee delivery of packets;
- not easy to replace protocols in TCP/IP;
- doesn't clearly separate the concepts of services, interfaces and protocols so not good for describing new technologies in new networks; and
- especially vulnerable to a SYN (synchronization) attack, which is a type of denial-of-service attack in which a bad actor uses TCP/IP protocol.
HTTPS
HTTP2 protocol
HTML definitions include the options to run HTTP2 services
https://html.spec.whatwg.org/multipage/server-sent-events.html
issue> servers drop http connections
Legacy proxy servers are known to, in certain cases, drop HTTP connections after a short timeout. To protect against such proxy servers, authors can include a comment line (one starting with a ':' character) every 15 seconds or so.
issue> Avoid http chunking is using event-stream connections
HTTP chunking can have unexpected negative effects on the reliability of this protocol, in particular if the chunking is done by a different layer unaware of the timing requirements. If this is a problem, chunking can be disabled for serving event streams.
issue> Client HTTP per server connection limitations
Clients that support HTTP's per-server connection limitation might run into trouble when opening multiple pages from a site if each page has an EventSource to the same domain. Authors can avoid this using the relatively complex mechanism of using unique domain names per connection, or by allowing the user to enable or disable the EventSource functionality on a per-page basis, or by sharing a single EventSource object using a shared worker.
migrating to HTTP2
https://dev.to/lek890/the-http-1-1-to-http-2-transition-for-web-apps-2bjm
routing HTTP2 traffic ( Tanzu concepts only )
https://docs.pivotal.io/application-service/2-12/devguide/http2-protocol.html
HTTP2 features and design
https://www.smashingmagazine.com/2016/02/getting-ready-for-http2/
HTTP2 features:
- allow concurrent requests across a single TCP connection, known as multiplexing;
- allow browsers to prioritize assets so that resources vital to the display of a page could be sent by the server first;
- compress and reduce HTTP headers;
- implement server push, whereby a server can push vital resources to the browser before being asked for them.
Confirm that a server app and Chrome are running HTTP2 not falling back to HTTP1
Is the client app and server running HTTP2? ( required for useful SSE without connection limits over the single TLS connection )
for chrome browser, validate the app is running on a TLS server using HTTP2
chrome://net-internals/#http2 creates an option to capture http logs to file - scan for HTTP2 in log
HTTP2 performance
https://web.dev/performance-http2/
It is important to note that HTTP/2 is extending, not replacing, the previous HTTP standards. The application semantics of HTTP are the same, and no changes were made to the offered functionality or core concepts such as HTTP methods, status codes, URIs, and header fields. These changes were explicitly out of scope for the HTTP/2 effort. That said, while the high-level API remains the same, it is important to understand how the low-level changes address the performance limitations of the previous protocols. Let’s take a brief tour of the binary framing layer and its features.
HTTP2 terms
- Stream: A bidirectional flow of bytes within an established connection, which may carry one or more messages.
- Message: A complete sequence of frames that map to a logical request or response message.
- Frame: The smallest unit of communication in HTTP/2, each containing a frame header, which at a minimum identifies the stream to which the frame belongs.
HTTP2 multiplexing - one connection per origin with optional stream prioritization
HTTP/2 provides a set of simple building blocks that allow the client and server to implement their own stream- and connection-level flow control:
https://web.dev/performance-http2/
SSE server-sent events doc
...