| Table of Contents |
|---|
...
| Reference_description_with_linked_URLs_______________________ | Notes______________________________________________________________ |
|---|---|
| NIST cybersecurity | |
| NIST cybersecurity framework | |
| NIST cybersecurity measurement | |
| FTC summary of NIST cybersecurity framework | |
| Synopsys summary of NIST cybersecurity framework. | |
https://www.fedramp.gov/program-basics/ | a cost-effective, risk-based approach for the adoption and use of cloud services by the federal government. |
https://www.fedramp.gov/assets/resources/training/100-A-FedRAMP-Training-Welcome-to-FedRAMP.pdf | |
| https://www.fedramp.gov/documents-templates/ | |
| fedramp - Understanding the Transition from Rev. 4 to Rev. 5). | |
https://www.fedramp.gov/assets/resources/documents/ | |
| ACCELERATING GOVERNMENT INNOVATION AND MODERNIZATION WITH CLOUD - Splunk | |
...
NIST-CSF-GUIDE_v2-implementation.pdf. file
NIST Cybersecurity Advisories
Advisory - 250317 - Medusa Ransomware
- Mitigate known vulnerabilities by ensuring operating systems, software, and firmware are patched and up to date within a risk-informed span of time.
- Segment networks to restrict lateral movement from initial infected devices and other devices in the same organization.
- Filter network traffic by preventing unknown or untrusted origins from accessing remote services on internal systems.
Note: This advisory uses the MITRE ATT&CK® Matrix for Enterprise framework, version 16. See the MITRE ATT&CK Tactics and Techniques section of this advisory for a table of the threat actors’ activity mapped to MITRE ATT&CK tactics and techniques.
Background
The RaaS Medusa variant has been used to conduct ransomware attacks from 2021 to present. Medusa originally operated as a closed ransomware variant, meaning all development and associated operations were controlled by the same group of cyber threat actors. While Medusa has since progressed to using an affiliate model, important operations such as ransom negotiation are still centrally controlled by the developers. Both Medusa developers and affiliates—referred to as “Medusa actors” in this advisory—employ a double extortion model, where they encrypt victim data and threaten to publicly release exfiltrated data if a ransom is not paid.
Medusa IABs (affiliates) are known to make use of common techniques, such as:
- Phishing campaigns as a primary method for stealing victim credentials [T1566].
- Exploitation of unpatched software vulnerabilities [T1190] through Common Vulnerabilities and Exposures (CVEs) such as the ScreenConnect vulnerability CVE-2024-1709 [CWE-288: Authentication Bypass Using an Alternate Path or Channel] and Fortinet EMS SQL injection vulnerability [CVE-2023-48788 [CWE 89: SQL Injection].
FBI has observed Medusa actors using the following tools to support command and control (C2) and evade detection:
- Ligolo.
- A reverse tunneling tool often used to create secure connections between a compromised host and threat actor’s machine.
- Cloudflared.
- Formerly known as ArgoTunnel.
- Used to securely expose applications, services, or servers to the internet via Cloudflare Tunnel without exposing them directly.
Lateral Movement and Execution
Medusa actors use a variety of legitimate remote access software [T1219]; they may tailor their choice based on any remote access tools already present in the victim environment as a means of evading detection. Investigations identified Medusa actors using remote access software AnyDesk, Atera, ConnectWise, eHorus, N-able, PDQ Deploy, PDQ Inventory, SimpleHelp, and Splashtop. Medusa uses these tools—in combination with Remote Desktop Protocol (RDP) [T1021.001] and PsExec [T1569.002]—to move laterally [TA0008] through the network and identify files for exfiltration [TA0010] and encryption [T1486]. When provided with valid username and password credentials, Medusa actors use PsExec to:
- Copy (
-c) one script from various batch scripts on the current machine to the remote machine and execute it withSYSTEMlevel privileges (-s). - Execute an already existing local file on a remote machine with
SYSTEMlevel privileges. - Execute remote shell commands using
cmd /c.
One of the batch scripts executed by PsExec is openrdp.bat, which first creates a new firewall rule to allow inbound TCP traffic on port 3389:
netsh advfirewall firewall add rule name="rdp" dir=in protocol=tcp localport=3389 action=allow
Then, a rule to allow remote WMI connections is created:
netsh advfirewall firewall set rule group="windows management instrumentation (wmi)" new enable=yes
Finally, the registry is modified to allow Remote Desktop connections:
reg add "HKLM\SYSTEM\CurrentControlSet\Control\Terminal Server" /v fDenyTSConnections /t REG_DWORD /d 0 /f
Mimikatz has also been observed in use for Local Security Authority Subsystem Service (LSASS) dumping [T1003.001] to harvest credentials [TA0006] and aid lateral movement.
Exfiltration and Encryption
Medusa actors install and use Rclone to facilitate exfiltration of data to the Medusa C2 servers [T1567.002] used by actors and affiliates. The actors use Sysinternals PsExec, PDQ Deploy, or BigFix [T1072] to deploy the encryptor, gaze.exe, on files across the network—with the actors disabling Windows Defender and other antivirus services on specific targets. Encrypted files have a .medusa file extension. The process gaze.exe terminates all services [T1489] related to backups, security, databases, communication, file sharing and websites, then deletes shadow copies [T1490] and encrypts files with AES-256 before dropping the ransom note. The actors then manually turn off [T1529] and encrypt virtual machines and delete their previously installed tools [T1070].
Indicators of Compromise
Table 1 lists the hashes of malicious files obtained during investigations.
| Files | Hash (MD5) | Description |
|---|---|---|
| !!!READ_ME_MEDUSA!!!.txt | Redacted | Ransom note file |
| openrdp.bat | 44370f5c977e415981febf7dbb87a85c | Allows incoming RDP and remote WMI connections |
| pu.exe | 80d852cd199ac923205b61658a9ec5bc | Reverse shell |
Table 2 includes email addresses used by Medusa actors to extort victims; they are exclusively used for ransom negotiation and contacting victims following compromise. These email addresses are not associated with phishing activity conducted by Medusa actors.
Potential Value Opportunities
Norton AVI protection for ransomware
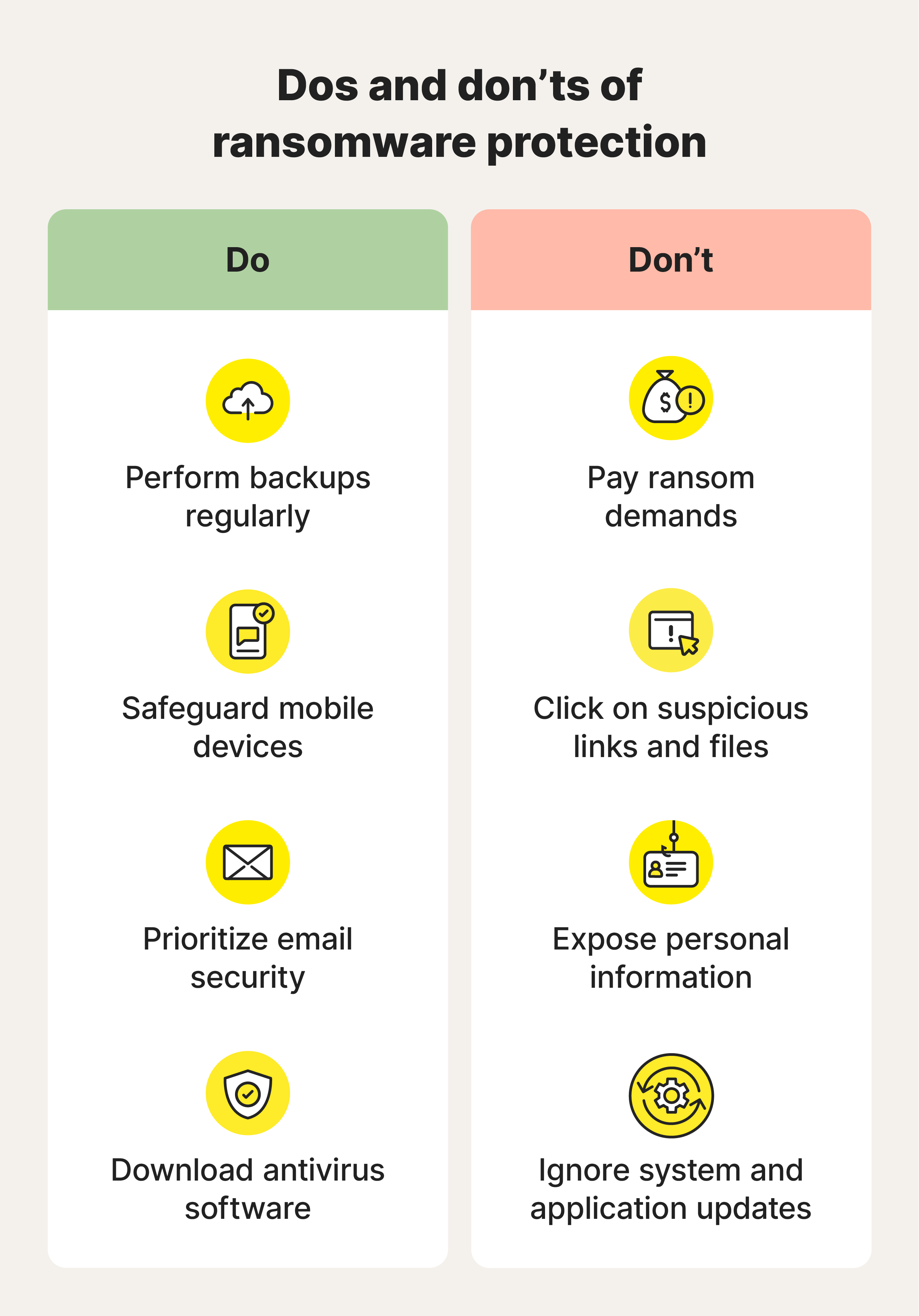
Ransomware protection includes a proactive action plan that covers what to do before, during, and after an attack. It’s a multi-layered approach that includes installing antivirus software, securing accounts, and having a recovery plan to mitigate risks associated with ransomware attacks.
Here is more detail on how the three-stage ransomware protection process works:
1. Prevention:
- Antivirus software: Install and maintain comprehensive security software that actively monitors for and helps block ransomware attempts.
- Regular backups: Create regular backups to secure cloud storage or external drives to protect your data so you always have access even if your devices are compromised.
- Avoid suspicious links: Be wary of suspicious links that could lead to malware. Exercise caution with links in emails and web pages. Hover over links to verify their legitimacy, especially in unsolicited communications.
2. Management:
- Isolate devices: Disconnect infected devices from networks to prevent the ransomware from spreading.
- Remove the malware: Use trusted security tools to eliminate the ransomware from affected devices or systems.
- Secure accounts: Immediately change passwords for all affected accounts using a secure device.
- Inform relevant parties: Notify those who are impacted or could be potentially impacted, such as family members or coworkers.
3. Recovery:
- Report the incident: File reports with relevant authorities, including local law enforcement, the Federal Trade Commission (FTC), and the Internet Crime Complaint Center (IC3).
- Investigate the cause: Analyze how the attack occurred to strengthen defenses against future incidents.
- Assess the damage: Document all affected systems and data to guide recovery efforts.
Potential Challenges
Candidate Solutions
...