Ethereum ERC 4337 Account Abstraction
Key Points
- Account Abstraction is a concept that turns users' wallets into smart contract accounts, in order to make Ethereum wallets more user-friendly and to prevent any loss of crypto keys
References
| Reference_description_with_linked_URLs_______________________ | Notes______________________________________________________________ |
|---|---|
| https://medium.com/infinitism/erc-4337-account-abstraction-without- ethereum-protocol-changes-d75c9d94dc4a | ERC 4337: account abstraction without Ethereum protocol changes |
| https://eips.ethereum.org/EIPS/eip-4337 | EIP 4337 |
Key Concepts
EIP 4337 concepts
https://eips.ethereum.org/EIPS/eip-4337
An account abstraction proposal which completely avoids the need for consensus-layer protocol changes. Instead of adding new protocol features and changing the bottom-layer transaction type, this proposal instead introduces a higher-layer pseudo-transaction object called a UserOperation. Users send UserOperation objects into a separate mempool. A special class of actor called bundlers package up a set of these objects into a transaction making a handleOps call to a special contract, and that transaction then gets included in a block.
What is EIP 4337 ? video
https://www.youtube.com/watch?v=Nsqyt7YYvgg
EOA - Externally Owned Account can use a Wallet service instead of a physical wallet reducing risks, providing better governance
SCA ( Smart Contract Account ) can be used as someone's primary account
q>> can an EOA have multiple SCAs?
yes, EOAs map to SCAs as owners
ERC 4337: account abstraction without Ethereum protocol changes
ERC 4337 account abstraction without Ethereum protocol changes.pdf link
ERC 4337 account abstraction without Ethereum protocol changes.pdf file
Account abstraction has for a long time been a dream of the Ethereum developer community. Instead of EVM code just being used to implement the logic of applications, it would also be used to implement the verification logic (nonces, signatures…) of individual users’ wallets. This would open the door for creativity in wallet designs that could provide some important features:
- Multisigs and social recovery
- More efficient and simpler signature algorithms (eg. Schnorr, BLS)
- Post-quantum safe signature algorithms (eg. Lamport, Winternitz)
- Upgradeability
It is possible to do all of these things with smart contract wallets today, but the fact that the Ethereum protocol itself requires everything to be packaged in a transaction originating from an ECDSA-secured externally-owned account (EOA) makes this very difficult. Every user operation needs to be wrapped by a transaction from an EOA, adding 21000 gas of overhead. The user needs to either have ETH in a separate EOA to pay for gas, and manage balances in two accounts, or rely on a relay system, which are typically centralized.
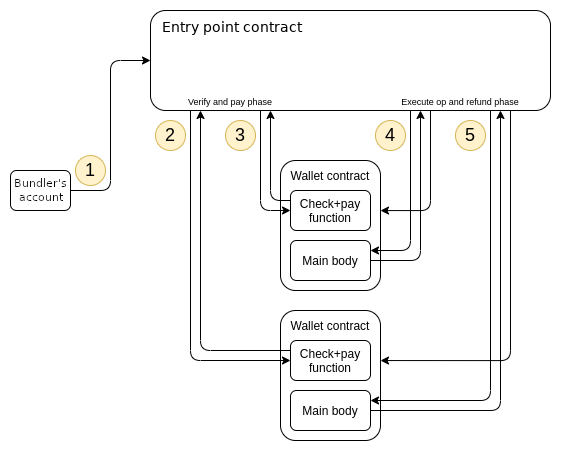
What a 4337 wallet contract does
A wallet is a smart contract, and is required to have two functions:
validateUserOp, which takes aUserOperationas input. This function is supposed to verify the signature and nonce on theUserOperation, pay the fee and increment the nonce if verification succeeds, and throw an exception if verification fails.- An op execution function, that interprets calldata as an instruction for the wallet to take actions. How this function interprets the calldata and what it does as a result is completely open-ended; but we expect most common behavior would be to parse the calldata as an instruction for the wallet to make one or more calls.
To simplify the wallet’s logic, much of the complicated smart contract trickery needed to ensure safety is done not in the wallet itself, but in a global contract called the entry point. The validateUserOp and execution functions are expected to be gated with require(msg.sender == ENTRY_POINT), so only the trusted entry point can cause a wallet to perform any actions or pay fees. The entry point only makes an arbitrary call to a wallet after validateUserOp with a UserOperation carrying that calldata has already succeeded, so this is sufficient to protect wallets from attacks. The entry point is also responsible for creating a wallet using the provided initCode if the wallet does not exist already.
Bundlers and mempool nodes can use logic similar to today’s Ethereum transaction handling logic to determine whether or not to include or forward a UserOperation.
Restrictions on the wallet contract operations in mem pool
There are some restrictions that mempool nodes and bundlers need to enforce on what validateUserOp can do: particularly, the validateUserOp execution cannot read or write storage of other contracts, it cannot use environment opcodes such as TIMESTAMP, and it cannot call other contracts unless those contracts are provably not capable of self-destructing. This is needed to ensure that a simulated execution of validateUserOp, used by bundlers and UserOperation mempool nodes to verify that a given UserOperation is okay to include or forward, will have the same effect if it is actually included into a future block.
How it works - bundle user operations in a mem pool
Instead of modifying the logic of the consensus layer itself, we replicate the functionality of the transaction mempool in a higher-level system. Users send UserOperation objects that package up the user’s intent along with signatures and other data for verification. Either miners or bundlers using services such as Flashbots can package up a set of UserOperation objects into a single “bundle transaction”, which then gets included into an Ethereum block.
The bundler pays the fee for the bundle transaction in ETH, and gets compensated though fees paid as part of all the individual UserOperation executions. Bundlers would choose which UserOperation objects to include based on similar fee-prioritization logic to how miners operate in the existing transaction mempool. A UserOperation looks like a transaction; it’s an ABI-encoded struct that includes fields such as:
sender: the wallet making the operationnonceandsignature: parameters passed into the wallet’s verification function so the wallet can verify an operationinitCode: the init code to create the wallet with if the wallet does not exist yetcallData: what data to call the wallet with for the actual execution step
What properties does this design add, maintain and sacrifice compared to the regular Ethereum transaction mempool?
Maintained properties:
- No centralized actors; everything is done through a peer-to-peer mempool
- DoS safety (a
UserOperationthat passes simulation checks is guaranteed to be includable until thesenderhas another state change, which would require the attacker to pay 7500+ gas persender) - No user-side wallet setup complexity: users do not have to care about whether or not their wallet contract has been “already published”; wallets exist at deterministic CREATE2 addresses, and if a wallet does not yet exist the first
UserOperationcreates it automatically - Full EIP 1559 support, including fee-setting simplicity (users can set a fixed fee premium and a high max total fee, and expect to be included quickly and charged fairly)
- Ability to replace-by-fee, sending a new
UserOperationwith a significantly higher premium than the old one to replace the operation or get it included faster
New benefits:
- Verification logic flexibility: the
validateUserOpfunction can add arbitrary signature and nonce verification logic (new signature schemes, multisig…) - Sufficient to make the execution layer quantum-safe: if this proposal gets universally adopted, no further work on the execution layer needs to be done for quantum-safety. Users can individually upgrade their wallets to quantum-safe ones. Even the wrapper transaction is safe, as the miner can use a new freshly created and hence hash-protected EOA for each bundle transaction and not publish the transaction before it is added in a block.
- Wallet upgradeability: wallet verification logic can be stateful, so wallets can change their public keys or (if published with DELEGATECALL) upgrade their code entirely.
- Execution logic flexibility: wallets can add custom logic for the execution step, eg. making atomic multi-operations (a key goal of EIP 3074)
Weaknesses:
- Slightly increased DoS vulnerability despite the protocol’s best effort, simply because verification logic is allowed to be somewhat more complex than the status quo of a single ECDSA verification.
- Gas overhead: somewhat more gas overhead than regular transactions (though made up for in some use cases by multi-operation support).
- One transaction at a time: accounts cannot queue up and send multiple transactions into the mempool. However, the ability to do atomic multi-operations makes this feature much less necessary.
Sponsorship with paymasters
Sponsored transactions have a number of key use cases. The most commonly cited desired use cases are:
- Allowing application developers to pay fees on behalf of their users
- Allowing users to pay fees in ERC20 tokens, with a contract serving as an intermediary to collect the ERC20s and pay in ETH
This proposal can support this functionality through a built-in paymaster mechanism. A UserOperation can set another address as its paymaster. If the paymaster is set (ie. nonzero), during the verification step the entry point also calls the paymaster to verify that the paymaster is willing to pay for the UserOperation. If it is, then fees are taken out of the paymaster’s ETH staked inside the entry point (with a withdrawal delay for security) instead of the wallet. During the execution step, the wallet is called with the calldata in the UserOperation as normal, but after that the paymaster is called with postOp.
Example workflows for the above two use cases are:
- The paymaster verifies that the
paymasterDatacontains a signature from the sponsor, verifying that the sponsor is willing to pay for theUserOperation. If the signature is valid, the paymaster accepts and the fees for theUserOperationget paid out of the sponsor’s stake. - The paymaster verifies that the
senderwallet has enough ERC20 balance available to pay for theUserOperation. If it does, the paymaster accepts and pays the ETH fees, and then claims the ERC20 tokens as compensation in thepostOp(if thepostOpfails because theUserOperationdrained the ERC20 balance, the execution will revert andpostOpwill get called again, so the paymaster always gets paid). Note that for now, this can only be done if the ERC20 is a wrapper token managed by the paymaster itself.
Note particularly that in the second case, the paymaster can be purely passive, perhaps with the exception of occasional rebalancing and parameter re-setting. This is a drastic improvement over existing sponsorship attempts, that required the paymaster to be always online to actively wrap individual transactions.
How far along is this proposal? > running in mainnet in March 2023
ERC 4337 can be found here. There is an implementation in progress here.
Potential Value Opportunities
Potential Challenges
Candidate Solutions
Step-by-step guide for Example
sample code block